
Risk analysts following the exercise of LightBasin, a financially motivated group of hackers, report the invention of a beforehand unknown Unix rootkit that’s used to steal ATM banking knowledge and conduct fraudulent transactions.
The actual group of adversaries has been just lately noticed focusing on telecom corporations with customized implants, whereas again in 2020, they had been noticed compromising managed service suppliers and victimizing their purchasers.
In a brand new report by Mandiant, researchers current additional proof of LightBasin exercise, specializing in financial institution card fraud and the compromise of essential programs.
Tapping into your banking knowledge
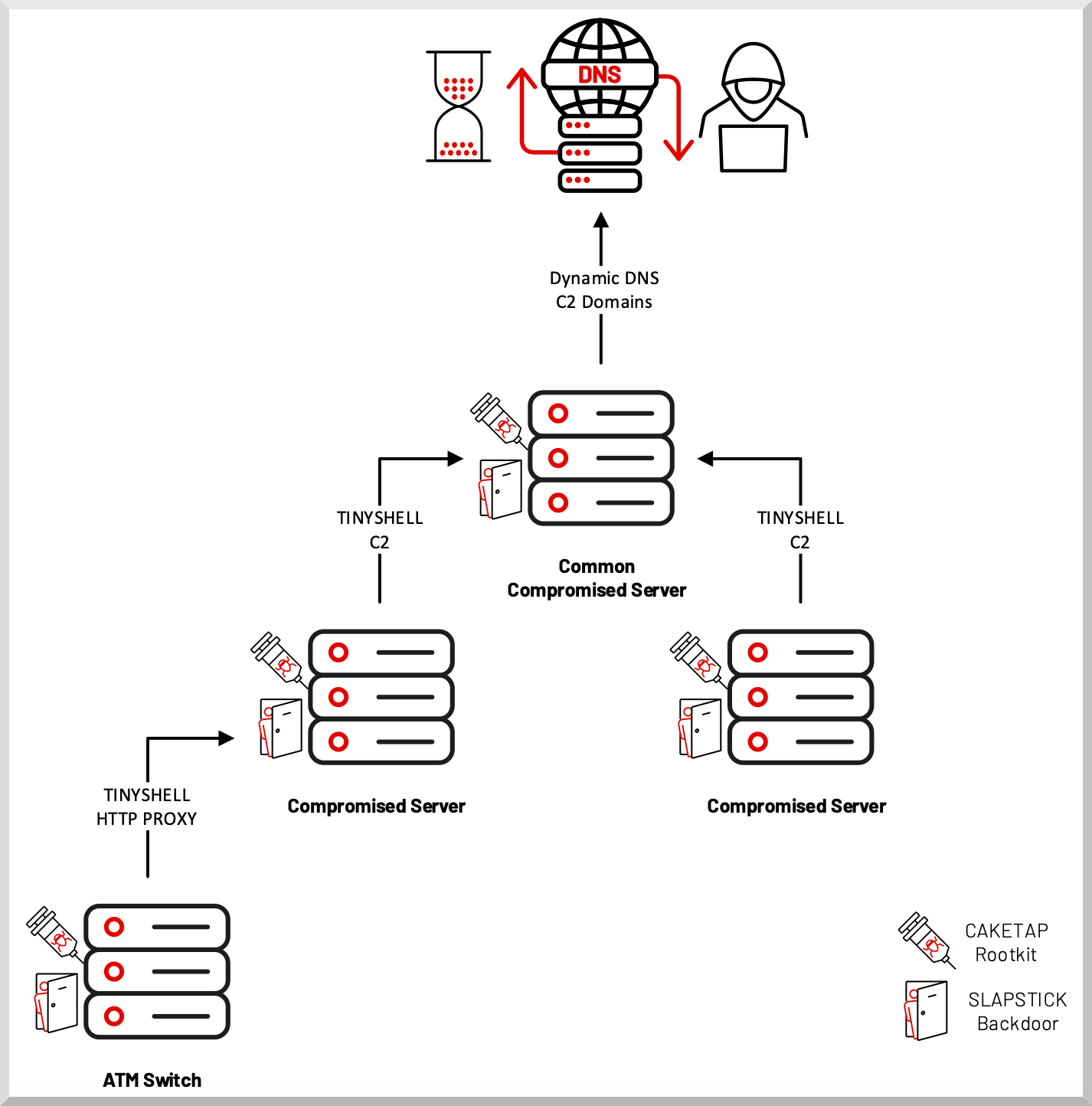
LightBasin’s new rootkit is a Unix kernel module named “Caketap” that’s deployed on servers working the Oracle Solaris working system.
When loaded, Caketap hides community connections, processes, and recordsdata whereas putting in a number of hooks into system capabilities to obtain distant instructions and configurations.
The instructions noticed by the analysts are the next:
- Add the CAKETAP module again to the loaded modules record
- Change the sign string for the getdents64 hook
- Add a community filter (format p)
- Take away a community filter
- Set the present thread TTY to to not be filtered by the getdents64 hook
- Set all TTYs to be filtered by the getdents64 hook
- Shows the present configuration
The final word purpose of Caketap is to intercept banking card and PIN verification knowledge from breached ATM swap servers after which use the stolen knowledge to facilitate unauthorized transactions.
The messages intercepted by Caketap are destined for the Fee {Hardware} Safety Module (HSM), a tamper-resistant {hardware} gadget used within the banking trade for producing, managing, and validating cryptographic keys for PINs, magnetic stripes, and EMV chips.
Caketap manipulates the cardboard verification messages to disrupt the method, stops people who match fraudulent financial institution playing cards, and generates a legitimate response as an alternative.
In a second part, it saves legitimate messages that match non-fraudulent PANs (Main Account Numbers) internally and sends them to the HSM in order that routine buyer transactions aren’t affected and the implant operations stay stealthy.
“We consider that CAKETAP was leveraged by UNC2891 (LightBasin) as half of a bigger operation to efficiently use fraudulent financial institution playing cards to carry out unauthorized money withdrawals from ATM terminals at a number of banks,” explains Mandiant’s report.
Different instruments linked to the actor in earlier assaults embody Slapstick, Tinyshell, Steelhound, Steelcorgi, Wingjook, Wingcrack, Binbash, Wiperight, and the Mignogcleaner, all of which Mandiant confirmed as nonetheless deployed in LightBasin assaults.
Subtle focusing on
LightBasin is a extremely skillful risk actor that takes benefit of relaxed safety in mission-critical Unix and Linux programs which are typically handled as intrinsically safe or largely ignored as a consequence of their obscurity.
That is exactly the place adversaries like LightBasic thrive, and Mandiant expects them to proceed to capitalize on the identical operational technique.
As for attribution, the analysts noticed some overlaps with the UNC1945 risk cluster however don’t have any concrete hyperlinks to attract protected conclusions on that entrance but.